When implementing your cloud security architecture, organizations must carefully consider various factors to ensure comprehensive protection. The availability of native security tools from cloud providers and specialized offerings from cloud security vendors add complexity to the decision-making process. With a multitude of options available, organizations face the challenge of selecting the most suitable tools and strategies to architect their cloud security effectively.
To enhance cloud security, organizations must assess specific requirements and bridge any gaps. Cloud providers offer native tools like encryption and threat detection, while security vendors provide additional specialized tools for advanced protection. Balancing the use of native tools and vendor offerings, organizations should evaluate capabilities and consider factors such as scalability and cost-effectiveness.
This infographic, created using an extract from the "4 Step Guide to Implementing Cloud Security", explores what specific considerations could be taken to ensure the most comprehensive protection for your organization when implementing cloud security.
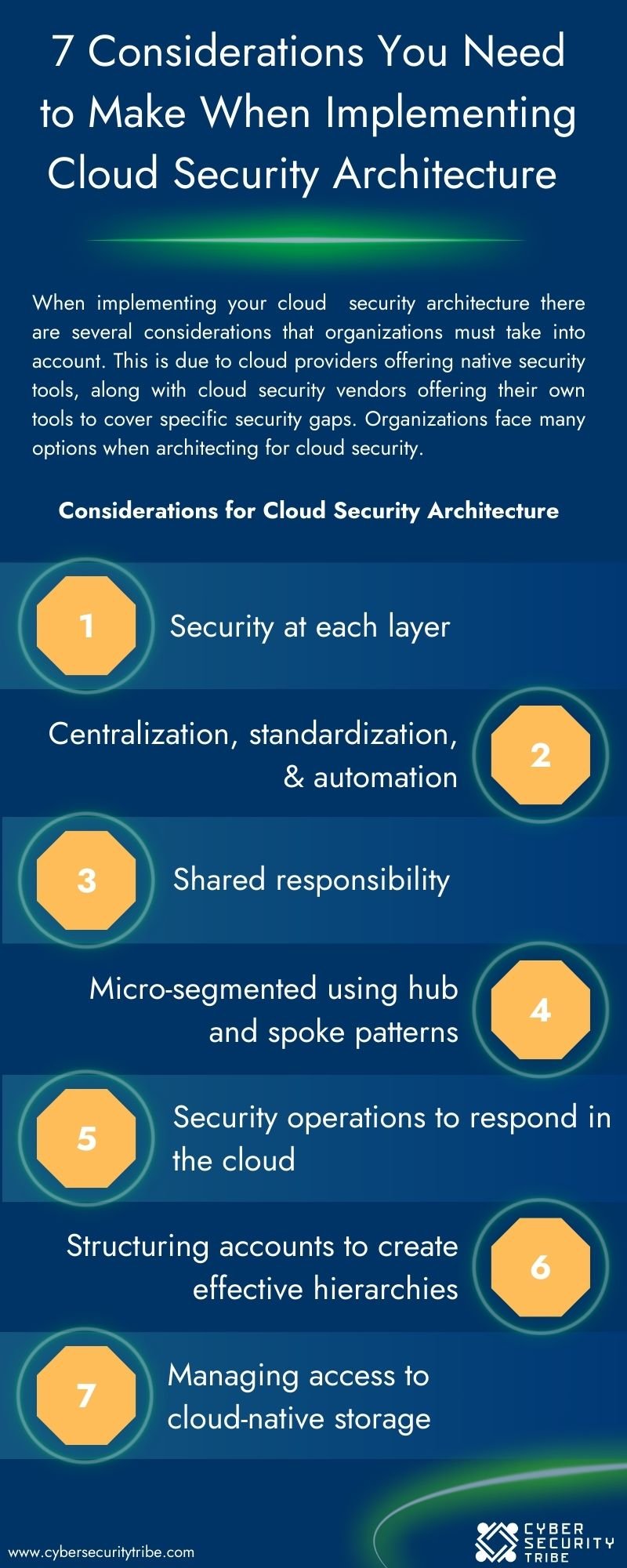
Organizations must navigate the landscape of security options when implementing their cloud security architecture. By considering the native security tools offered by cloud providers and leveraging specialized offerings from cloud security vendors, organizations can build a robust and comprehensive security framework. With a well-architected cloud security infrastructure in place, organizations can confidently embrace the benefits of the cloud while safeguarding their data and applications against potential threats.