Scanner.dev Announces Detection Rules as Code
Leveraging Github for stronger collaboration, change management and continuous delivery of detection rules
Scanner.dev, a next-gen SIEM and observability platform, is excited to announce the release of Detection Rules as Code, allowing security teams to manage Scanner detection rules directly in their own Github repositories. This enables stronger collaboration, change management, and continuous delivery of detections.
Detection rules are a critical component of any security monitoring system, allowing teams to run continuous queries to identify potential threats or misconfigurations.
Powerful detection queries. Fast historical backtesting.
Teams can leverage the full power of Scanner queries in their detection rules. Scanner executes these queries on the data live as it is indexed. This gives teams the ability to detect threats immediately across sliding time windows, ranging from one minute to one day.
Because of Scanner’s unique search speed, detection rule queries can be backtested against historical data rapidly. The speed of full data scans (eg. looking for unusual spikes in common log event types) is typically 300 - 500 GB/second, and the speed of needle-in-haystack searches (eg. looking for IP addresses or file hashes) is typically 8 - 10 TB/second.
Built-in CI/CD
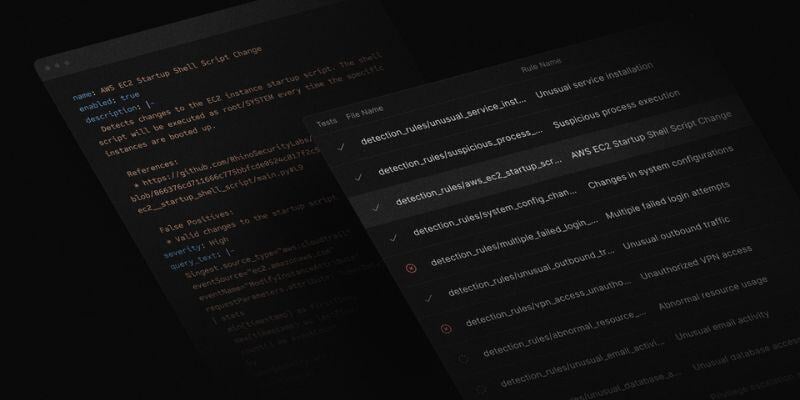
By storing detection rules in a Github repository, teams can now collaborate on detection rule changes using familiar pull request workflows. Scanner takes this a step further by providing built-in CI/CD. Upon pushing changes to a configured branch, Scanner automatically runs all tests defined in the detection rules. When the tests pass, the rules are deployed to the user’s Scanner instance.
Out-of-the-box detection rules
Scanner now provides 100+ out-of-the-box detection rules, available in public Github repositories. These cover popular data sources like AWS CloudTrail, Okta, and Windows process creation events, with more to come. Teams can use these as a starting point, customizing them to their specific environments.
Getting started
“Threat detections are one of the most important pillars of SIEMs, and we’re excited to help users streamline their threat detection development lifecycle,” said Cliff Crosland, CEO of Scanner. “By embracing software development practices like code reviews, testing, and CI/CD, teams can develop and deploy detections faster.”
Teams can follow these steps to get started.
- Install the Scanner Github app into your Github organization or into a specific repository.
- In the Scanner UI, choose the repository and branch to use for deployment, eg. main.
- Edit detection rules in your repository and push to the deployment branch. Scanner will validate the rules and run tests. If tests are successful, the rules will synchronize to your Scanner instance.
- In detection rules, you can configure the destinations where alert events are sent by specifying event sinks, like Slack, Torq, or custom webhooks.
Detection Rules as Code is available immediately to all Scanner customers. For more information, visit https://scanner.dev or contact your account engineer.
About Scanner:
Scanner is a next-generation SIEM and observability platform giving customers unprecedented visibility and threat detection on their cloud security logs. Using a novel query engine designed from the ground up for cloud storage, customers can analyze petabytes of data at speeds of up to 10TB per second, at 80-90% less cost than legacy tools. It’s time for SIEMs to scale up.
