From Defects to Dollars (Part 2) - Business Decisions
In part 1 of this multi-part series, we established an outline for the series and linked to several free downloadable digital tools. Then, we briefly provided a primer on value creation using the 5Ws + H framework. That is to say, we reviewed the who, what, where, when, why, and how of value.
If you haven’t read that post already, you may be missing some context for this discussion.
Yogi Berra once said, “In theory, there is no difference between theory and practice. In practice, there is.” The quote is both funny and true. I mention the quote now because we're starting with a brief discussion on the scientific method. Then we’ll build in a touch of reality by examining the use of leading decision-making frameworks that can enhance our decision-making and help us over-determine decisions others make through choice architecture and influence strategies.
By the time you finish this post, you should have:
- A basic understanding of how decision science impacts your decisions and a reference framework to improve your own decisions.
- A basic understanding of how decision science impacts decisions others make and some complimentary tools to optimize choice architecture and a structured approach to develop influence plans.
- A clear picture of which tool (WRAP, Influencer, Choice Architecture) to use and when.
Scientific Method
“To place the scientific method in the context of decision-making, consider Ray Dalio's perspective that “while there is no one best way to make decisions, there are some universal rules for good decision making. They start with recognizing: A) the biggest threat to good decision-making is harmful emotions, and B) decision-making is a two-step process (first learning, and then deciding).”1
“Indeed, the scientific method is “a process for experimentation used to explore observations and answer questions…The goal is to discover cause and effect relationships by asking questions, carefully gathering and examining the evidence, and combining the available information into a logical answer.”2 The figure below illustrates the scientific method:
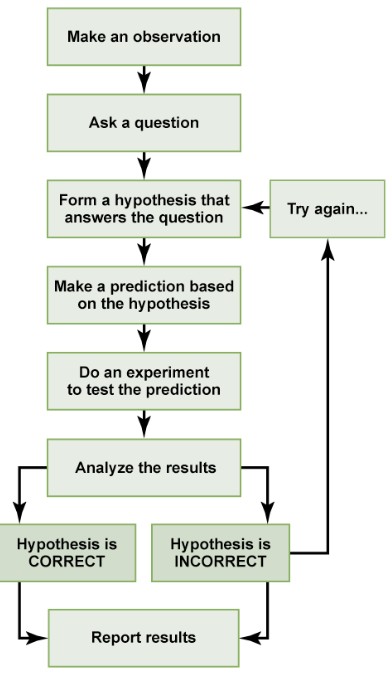 FIGURE 1: Flowchart of The Scientific Method - Source: Rice University / CC BY 4.0.
FIGURE 1: Flowchart of The Scientific Method - Source: Rice University / CC BY 4.0.
However, business decisions rarely follow such a structured approach. Even resource-rich companies, flush with cash and surrounded by data, may skip the rigor required to establish and test a hypothesis. Indeed, it is all too common that confirmation bias corrupts the analysis phase. Further, technical, statistical, or business comprehension issues affect the presenter and the audience.
Nevertheless, you can control your role in the decision process by keeping the scientific method present as you apply discipline and diligence to an objective and structured learning methodology.
Decision Science
No modern discussion of decision science should exclude Nobel Prize-winning psychologist Daniel Kahneman. His research supplied the foundation of behavioral economics and derived a new way of thinking about human error. At a minimum, we recommend reviewing his work, Thinking, Fast and Slow. However, you are in luck if you are not up for the full read because his research is summarized simply and interactively here: https://yourbias.is/.
If you think about a normal decision process, it usually proceeds in four steps. The book 'Decisive' explains that a villain afflicts each of these steps:
- “You encounter a choice. But narrow framing makes you miss options.
- You analyze your options. But the confirmation bias leads you to gather self-serving information.
- You make a choice. But short-term emotion will often tempt you to make the wrong one.
- Then you live with your choice. But you'll often be overconfident about how the future will unfold.”
I’ll defer to the WRAP process in Decisive to clarify how to improve your decision-making. In The CISO Evolution, we put the process to use in the context of cybersecurity.
Beyond using the WRAP process to improve my decision-making, I have successfully utilized tools such as the Influence Challenge Planner presented in Influencer: The New Science of Leading Change. Primarily this tool is helpful when attempting to drive cultural change or guide crucial decisions that others must make.
Choice Architecture
The section above offers techniques to mitigate the well-researched phenomenon of loss aversion, status quo, confirmation, and other biases in decision-making. Equipped with these strategies and an awareness of decision-making pitfalls, we divert our focus to choice architecture.
Here we will lean heavily on the work Nudge by Richard H. Thaler and Cass R. Sunstein. As they define a few terms, “A choice architect is responsible for organizing the context in which people make decisions. Further, a nudge is any aspect of choice architecture that predictably alters people's behavior without forbidding any options or significantly changing their economic incentives.”
My experience implementing cybersecurity across several organizations indicates that most people want to do the right thing. Yet, they might forget or avoid implementing security if it is too complicated or otherwise feel pressed for time. Most people will gladly comply with security requirements when given adequate encouragement and support. So, when are nudges helpful, and what are the most beneficial ways CISOs structure choices and nudge their organizations?
According to Thaler and Sunstein, nudges can be most helpful when offering benefits now and costs later (i.e., publish the feature today, and deal with a data breach later). Often people and organizations struggle with self-control and accountability. As the time between a choice and its consequences increases, so does the accountability gap.
Further, a nudge might help when:
- the frequency of action is low → such as software deployment in monolithic/waterfall environments
- the complexity of a decision is high → such as when answering the question - “what is the probability that we will experience a data breach this year?”
- the feedback offered along the way is limited → like 15 minutes in a quarterly board session.
- or the relationship between a choice and the subsequent experience is ambiguous → we have never experienced a data breach despite a lack of investment in XDR or monitoring tools!
Conclusion
In Post 1 of this multi-part series, I provided a primer on value creation. In this post, I’ve explained that most decisions are not entirely rational. Instead, they are subject to logical fallacies, and cognitive biases, not to mention the agency problem. So, using a structured approach to learn, decide, and influence can be potent in shifting culture, obtaining funding, and practically aligning to a risk appetite in the face of business operations.
Further, I’ve offered several resources to help you overcome common challenges. Specifically, we discussed the WRAP process, Influencer Challenge Planner, and the gentle power of nudges to help frame choices against an appropriate backdrop.
Next time we’ll decompose several helpful tools used to ARTICULATE THE BUSINESS CASE (Post 3). In particular, we will review stakeholder analysis, the business model canvas, and the emerging use of cyber risk quantification. In a final post, I’ll combine what we’ve learned in a CASE STUDY ON APPLICATION SECURITY VALUE ASSURANCE (Post 4).
References:
1: Dalio, R., Principles. Simon & Schuster, 2017.
2: “Science Buddies, “Steps of the Scientific Method.” Accessed October 8, 2020. https://www.sciencebuddies.org/science-fair-projects/science-fair/steps-of-the-scientific-method
Share this
You May Also Like
These Related Stories

Speaking CFO: Why I'm Bridging the Gap Between Security and Finance

Why Compliance-Driven Cybersecurity Governance Fails


