Run Security / Do Security for Value Assurance
Executive Insights:
- Executive Leaders should consider running information security like a business that creates tangible benefits for the organization.
- Assurance Leaders should adopt a strategic run/do model to bridge the gap between operational security functions and strategic Trust leadership.
- Trust Stakeholders play an important role in the revenue journey, so it is essential to address their concerns and create a trust context through high quality evidence assets.
- Value assurance provides Assurance leaders with a strategic model to demonstrate the influence of their practices on customer and revenue journeys.
- Communication models should be in place to tell credible stories that communicate trustworthiness to Trust Stakeholders such as customers, IT, privacy, legal, regulators, investors, etc.
Most organizations recognize the value of information security and compliance when it comes to protecting their assets. Strategic Assurance leaders understand that running InfoSec like a business can yield tangible benefits for the organization. By reframing the nature of value defense and transforming Information Security from a cost center into a strategic Revenue investment, organizations can increase Revenue velocity, secure premium valuation at equity events, and offer a “Trust Product” as a competitive differentiator. This management strategy is called Value Assurance and it is intended to be practiced by CISOs and CIOs who want to participate in the revenue, product, and customer journeys as accountable leader and enable and defend value for their organizations.
The Gap Between Do Security / Run Security
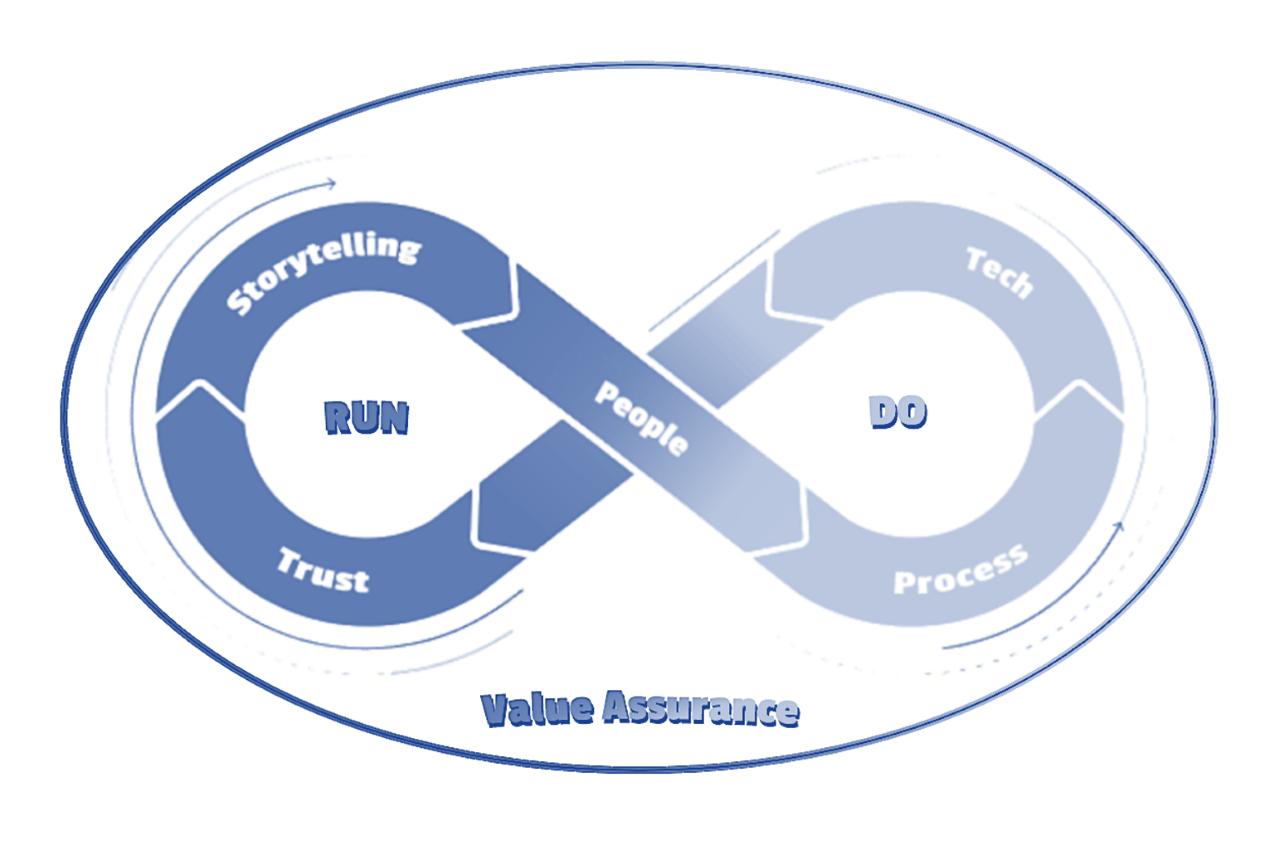
Defending organizations from crime and value loss is the core mission of information security. However, there are key business drivers that require a well-run Trust and Safety program: reducing Value Loss, meeting Customer Commitments, complying with Frameworks, Regulations & Statutes, meeting Market/Vertical Criteria, improving Insurability, increasing Equity Defense, and preventing Crime. This expanded mandate should lead one consider the scope of the mission. While InfoSec is often viewed as just a monitor/defend/comply function due to its focus on securing people, technology, and processes through controls and policy, there is a gap between operational “Do Security” (running security, privacy resilience, and compliance operations) and strategic “Run Security” (Trust leadership with Value impact). To bridge this gap, leaders should consider adopting a strategic Value Assurance RUN/DO model, aligning operational Trust & Safety under the Assurance organization, and focusing operational leadership on a Value Storytelling model.
DO Security: Defend and enable Technology, Processes, & People
RUN Security: Build and “Sell the Trust Product”, Tell Security Stories to Trust Stakeholders, Lead Trust Culture
Trust Stakeholders
Trust Stakeholders are actors in the Revenue journey with a Trust or Safety requirement that, if not satisfied, presents a risk to deal, relationship, or ability to engage at all. These stakeholders play a key role in the buyer and revenue journey, as they need to feel trust in your organization and services at various levels. Failing to address their concerns can create friction in revenue velocity that leads to risk to Value, resulting in material short-to-mid-term losses. The Assurance practice orchestrates Trust as its product, delivered to these Stakeholders via a Security Story communications model. Depending on the industry, Assurance leaders may encounter eleven (or more) Trust Stakeholders:
- The Customer Champion
- Customer IT
- Customer Privacy
- Customer Procurement
- Customer Legal
- Customer InfoSec
- Customer Compliance/Internal Audit
- Upstream Customer Regulator
- Upstream Customer Auditor
- Upstream Customer Insurer
- Customer’s Customers’ Trust Stakeholders
These Trust Stakeholders should be seen as personas in a Revenue playbook (not anonymous opposing operations personnel) that have varying touchpoints with your organization with often mandatory requirements for Trust & Safety. It is essential to orient the Assurance practice to continuously produce high quality evidence that will satisfy any Trust inquiries stemming from stakeholder engagement.
High quality evidence is key to an ongoing communications campaign aimed at proactively creating and maintaining a Trust context and is ultimately executed as a strategic pillar of the organizations’ Marketing story. Under a Value Assurance RUN/DO model, these eleven Value Stakeholders are ‘customers’ of the ‘trust product’ produced through EvidenceOps: the Assurance Operations practice of identifying, pulling, sorting, tagging, structuring, preparing, and presenting high quality evidence assets in support of a Security Story. Evidence Operations enables the practice of telling credible stories that communicate trustworthiness to these stakeholders. This requires organizing and communicating security, engineering, HR, Legal, and IT-Ops evidence as Story, typically as a curated library of Marketing artifacts and Revenue battlecards that are deployed in support of the go-to-market motion.
As transformational management practice, Value Assurance provides assurance leaders with a strategic model to demonstrate the influence of their practices on customer and revenue journeys. By creating a "trust product" for Trust Stakeholders as part of the go-to-market motion, Trust & Safety become differentiating factors in competitive markets. Aligning InfoSec with revenue strategy and running it like a Product practice can transform its utility to the business, potentially increasing investment in the function as its Value impact is demonstrated.
Share this
You May Also Like
These Related Stories

Why Security Leaders Must Work with HR to Stop Hiring Fraud

Security is an Infinite Game


